This is the guide that explains removal of Internet Security 2013 virus. This is a fake anti-spyware program with amsecure.exe as its core process. Classified as a rogue, the program obviously represents severe danger for your system. The ultimate purpose of fake AV programs is to scare and trick users into buying the fake licensed versions of them. This is the exact behavior of Internet Security 2013 scam once it enters infected computers. Once this hoax gets into systems with poor anti-malware protection it begins scanning drives and reporting the majority of clean files as ones infected with W32/Blaster.worm (fake and invented threat). Obviously, the variety of this and many other tricks of the rogue pursue the only goal – to prompt user into buying the fake protection from this program which can’t really function as a powerful computer security utility.
Here is how Internet Security 2013 scam looks like:
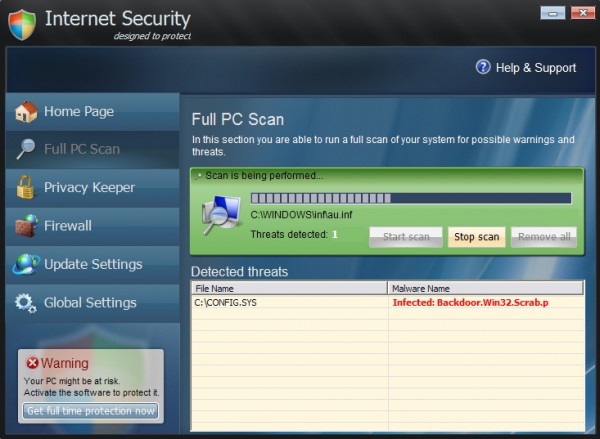
The rogue comes into computers without user’s approval or even consent. In many cases users don’t even know that this hoax is being installed onto their workstations. Yet, the malware is quite smart in bypassing the existing security barriers installed on targeted computers. So, not only it successfully installs itself without approval. Additionally, the malady modifies system settings to be self-started automatically with every system startup. As a result, turning the PC each time is the moment when Internet Security 2013 GUI comes up on the compromised machine.
Internet Security 2013 upon successful launching begins “scanning” attacked computer. We intentionally put the word scanning into quotation marks to emphasize the fake character of such outwardly decent behavior. In reality, the program simply finds certain files that are marked as threats, even through these are either legitimate Windows files or those ones that were invented by the rogue. This sequence of scary security warnings, notifications and obviously fake security alerts of Internet Security 2013 has in mind to make users believe their systems are in danger. The next step the rogue makes is quite predictable, since it is typical for all scarewares. Once scared users decides to remove all fake threats reported by the hoax, Internet Security 2013 offers users to buy its licensed version to make it possible.
If your system got attacked by Internet Security 2013 scam it’s time to remove this nasty malware off your system. We do hope you haven’t bought this scam. If you’ve done so by mistake, please immediately refer to your bank or other payment processing institution and dispute the charges made via your bank card or account. Explain to the bank officials that the program you’ve purchased is a fake anti-spyware application. Hopefully, you will get your money back. Finally, to get rid of Internet Security 2013 malware please follow the guidelines outlined below.
Typical fake alert of Internet Security 2013 virus:
Explorer.exe can not start
File Explorer.exe is infected by W32/Blaster.worm
Please activate Internet Security 2013 to protect your Computer.
Typical problems caused by the rogue:
- Stopping Task Manager by replacing it with its own, fake one.
- Terminating downloads of legitimate anti-malware applications.
- Blocking execution of available anti-spyware programs (already installed on attacked PC).
- Showing constant alerts, warnings and notices about bogus threats supposedly identified during the fake scanning.
- Tricking users into buying the license of the rogue.
- Possible browser redirection issues.
- Utter system slowdown.
Preparation to removal of Internet Security 2013 scam:
- Click “Start” menu and go to “Run” option. Type-in the following text exactly as it is specified here:
taskkill.exe /F /IM amsecure.exe
This will kill the process of Internet Security 2013 virus. (if you could not do it from the first attempt then try again)
- Download our recommended security software to your infected PC, install and run it.
- Remove all identified files and registry entries associated with the rogue anti-spyware, as well as other available threats.
Important! If this method didn’t help you kill the process of Internet Security virus, visit this guide https://www.system-tips.net/ruskill-exe-tool-to-kill-malware-by-window-title/ that will help you terminate the virus process using RusKill.exe application. Make sure you follow the instructions carefully!
Removal video guide:
Alternative solution to stop amsecure.exe (Internet Security 2013 process):
Internet Security 2013 manual removal:
Internet Security 2013 files:
%CommonAppData%\amsecure.exe
%Desktop%\Internet Security 2013.lnk
%Desktop%\Internet Security.lnk
Internet Security 2013 registry entries:
HKEY_CURRENT_USER\Software\
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “Internet Security 2013”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “Internet Security”
File Location Implications:
%Desktop% implies that the file is located straight on your PC’s desktop. The full and detailed location is C:\DOCUMENTS AND SETTINGS\Current User\Desktop\ for Windows 2000/XP, and C:\Users\Current User\Desktop\ for Windows Vista and Windows 7.
%Temp% stands for the Windows Temp folder. By default, it has the location C:\Windows\Temp for Windows 95/98/ME, C:\DOCUMENTS AND SETTINGS\Current User\LOCAL SETTINGS\Temp for Windows 2000/XP, and C:\Users\Current User\AppData\Local\Temp for Windows Vista and Windows 7.
%AppData% means the current users Application Data folder. By default, it has the location C:\Documents and Settings\Current User\Application Data for Windows 2000/XP. For Windows Vista and Windows 7 it is C:\Users\Current User\AppData\Roaming.
%StartMenu% stands for the Windows Start Menu. For Windows 95/98/ME the location is C:\windows\start menu\, for Windows XP, Vista, NT, 2000 and 2003 it stands for C:\Documents and Settings\Current User\Start Menu\, and for Windows Vista/7 it is C:\Users\Current User\AppData\Roaming\Microsoft\Windows\Start Menu.
%CommonAppData% means the Application Data folder in the All Users profile. For Windows XP, Vista, NT, 2000 and 2003 it has the location C:\Documents and Settings\All Users\Application Data\, and for Windows Vista/7 it is C:\ProgramData.

Comments are closed.