The Petya.A ransomware is one of the worst computer infections you will never want to face in your entire life. It is listed as the top file-encryption malware that penetrates into Windows PCs silently. The worst part of the story is that you can’t even prevent its intrusion! If you have access to the Internet it can attack your system. Our malware analysis team found that Petya Encryption Infection is packed on third party freeware and spam email attachments. How does it attack your particular PC? Please continue reading this guide.
Quick menu to help you navigate through Petya (Petya.A) removal guide.
Removal guide for Petya (Petya.A) malware.
Additional manual fixes for your browsers after malware attack.
Generally Petya.A ransomware attacks HR departments. It sends emails with pretty specific subjects – for example, CV. Seems like nothing to worry about, doesn’t it? The letters are accompanied by a link to the full portfolio of the applicant, the file of which is placed on Dropbox or some other network folder. Of course, instead of a portfolio, you will have an application named like portfolio-packed.exe. Once that has occurred on your system, it will drive you crazy. Petya Ransomware will encrypt all your personal data if you do not remove on a timely basis. Your documents, photos, emails, PDF files, music, movie, video and other types of files will be all affected. As time goes by, you will find that more and more files can’t be accessible anymore. Petya Ransomware shows you warning messages to tell you that you have to pay $300 in the equivalent of Bitcoin digital currency and send the money to the account of cyber frauds if you want to restore the encrypted files. It warns that you will be able to restore any files if you do not purchase the decryption key, and they will ruin all your files if you try any other way to recover your files. But it has been revealed that even after you pay the fees to exchange the decryption key, the restoration of your files cannot be 100% unambiguous. You may pay for nothing and still lose all your data. Hence, it’s best not to send any money to these cyber criminal.
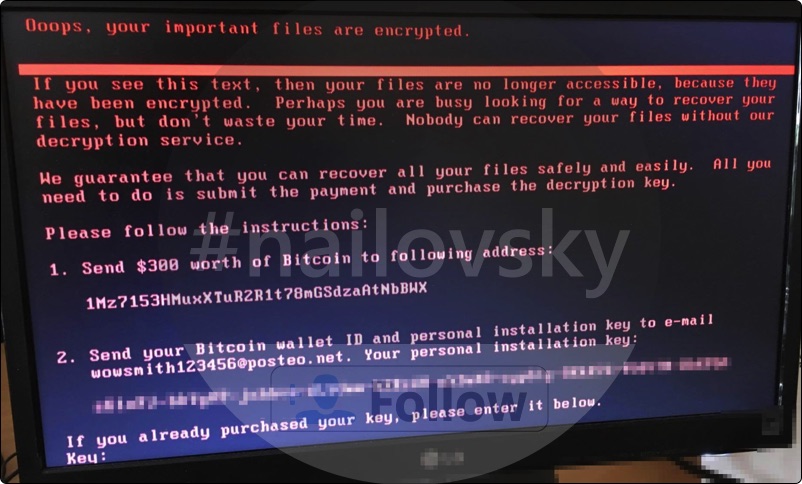
Fake alert mentioned by Petya.A ransomware is as follows:
Oops, your important files are encrypted.
If you see this text, then your files are no longer accessible, because they have been encrypted. Perhaps you are busy looking for a way to recover your files, bud don’t waste your time. Nobody can recover your files without our decryption service. We guarantee that you can recover all your files safely and easily. All you need to do is submit the payment and purchase the decryption key.
Please follow the instructions:
1. Send $300 worth of Bitcoin to following address.
2. Send your Bitcoin wallet ID and personal installation key to e-mail wowsmith123456@posteo.net. Your personal installation key.
At this moment, removal of Petya Ransomware will be the right action you should perform, thus you will have a slim chance to decrease the number of encrypted files and guarantee the safety of your system. After you delete Petya Ransomware completely, you can count on some famous software specialized in file restoring to recover some files. Now follow this guide to save your system and files.
Petya (Petya.A) removal instructions.
This slider below shows how to use Trojan Killer Portable for Petya (Petya.A) detection and removal:
Step-by-step guidelines.
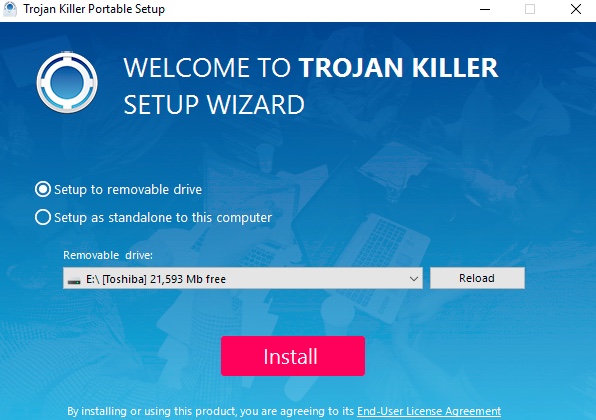
- Step 1. Download Trojan Killer Portable via the download button below:
- Step 2. Click on “Install” button and proceed with its installation process.
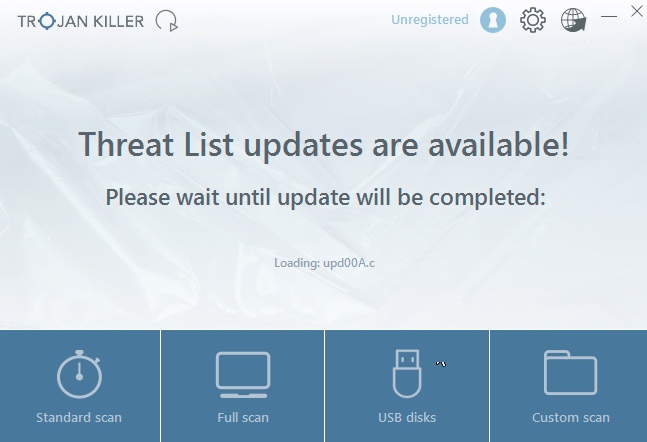
- Step 3. Select scan type.
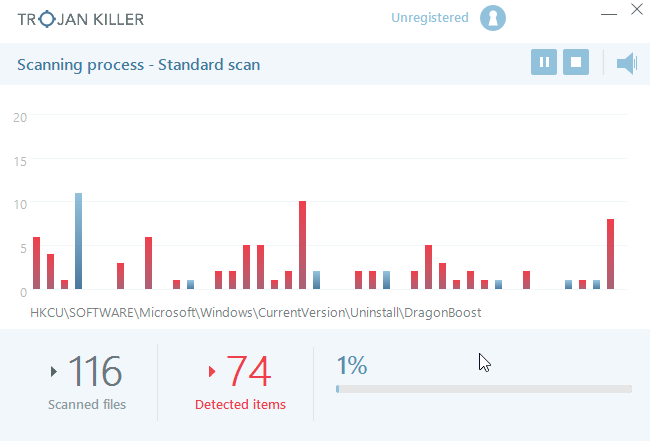
- Step 4. Software will begin scanning your system.
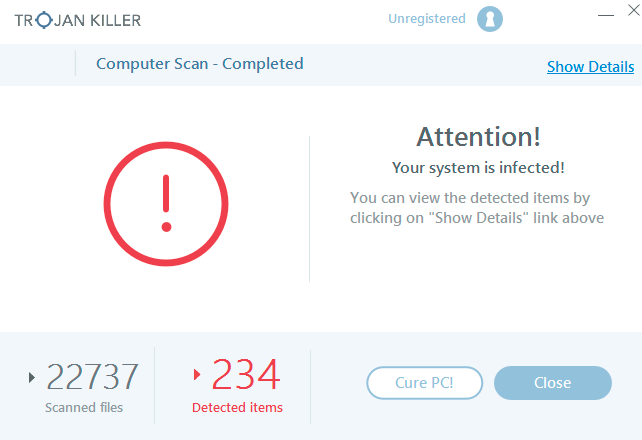
- Step 5. Click on “Cure PC“.
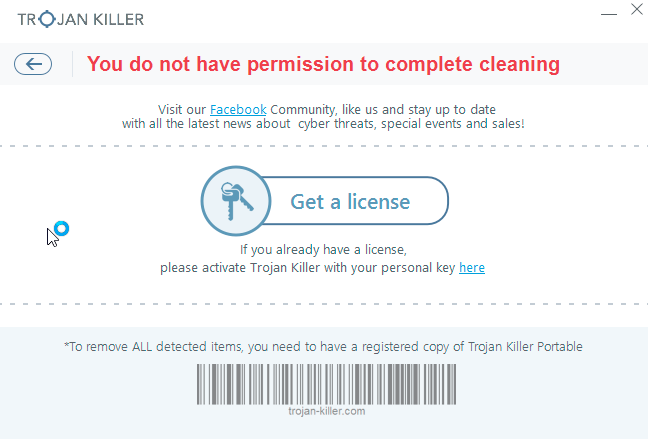
- Step 6. Click on “Get a license“.
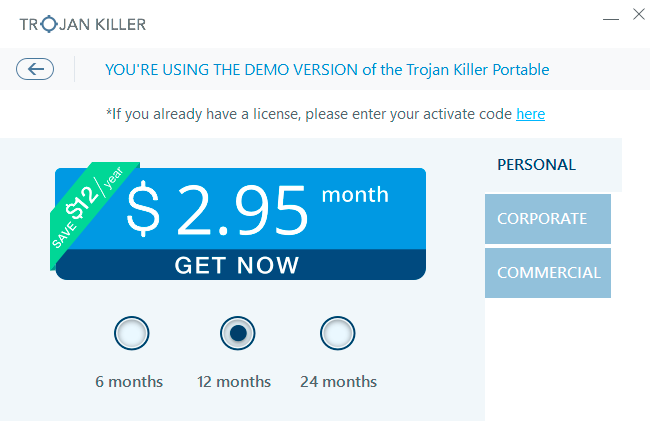
- Step 7. Select license term and purchase the program to remove malware.
Solution to protect your computer from getting contaminated with Petya (Petya.A) and similar threats in the future:
With millions of malicious applications currently in the web people definitely need powerful security solutions for their PCs. You could have avoided all negative side effects related to unwanted intrusion of adware with the help of Trojan Killer Portable, so we strongly advise that you buy Trojan Killer Portable now!
After you eliminate Petya (Petya.A) malware it is mandatory to apply additional manual fixes to clean your browsers from malware traces.
- In Google Chrome, click on the menu button in the upper-right part of the screen which either looks like three vertical dots. Scroll down to the bottom of the drop-down menu and click on "Settings" (as shown in one of the images above).
- Select "Extensions" in the left part of the window. Uncheck suspicious extension, then click on the Trash icon next to it.
- WARNING. Final optional steps. Use these steps only if the above-mentioned methods to remove malware from Google Chrome did not help. When in Google Chrome settings mode, scroll down to the bottom of the page and click on "Show advanced settings".
- Scroll down to the bottom of the page and click on "Reset settings" button.
- In the pop-up window, click on "Reset".
- In Mozilla Firefox, click on the icon that looks in the form of three horizontal lines in the upper-right section of the browser window. Click on "Add-ons".
- Click on the "Extensions" tab in the left part of the windows. Check suspicious extensions. If you identify them, click on "Disable", then on "Remove".
- NOTE. Final optional steps. Use these steps only if the above-mentioned methods to remove infection from Mozilla Firefox did not help. Click on the icon that looks in the form of three horizontal lines in the upper-right section of Mozilla Firefox and select the question-mark icon at the bottom of the drop-down menu.
- Click on "Troubleshooting information" in the slide-out menu.
- Select the "Refresh Firefox" button at the top right of the new web page.
- Finally, click on "Refresh Firefox" again to confirm the action.
- Click on Internet Explorer settings icon in the upper-right part of the browser in the form of a gear-wheel. Select "Manage add-ons".
- Find suspicious toolbar or extension. Click on it (make it highlighted). Then click on "Disable" button related to this particular toolbar or extension.
- NOTE. Final optional steps. Use these steps only if the above-mentioned methods to remove malware from Internet Explorer did not help. Click on Internet Explorer settings icon in the upper-right part of the browser in the form of a gear-wheel. Select "Internet Options".
- Select "Advanced" tab, then click on "Reset".
- Select appropriate reset options, then click on "Reset".
- Click on "Opera" menu in the upper-right part of the browser. Choose "Extensions", then click on "Manage extensions".
- If you detect anything suspicious, disable and delete it.
- Step 1. Click on "Safari" menu, then go to "Preferences".
- Step 2. In the "Extensions" tab, locate suspicious extensions and click on "Uninstall".
- Step 3. In Safari menu, select "Clear history" and click on "Clear History again".
- Step 4. Get back to Safari menu, then click on "Preferences".
- Step 5. Click on "Privacy" tab, then choose "Manage Website Data...".
- Step 6. Click on "Remove All", then on "Done".