This is the guide explaining general tips to fix browser redirection problem. Feel free to use it for removal of all browser hijackers that may attack Internet Explorer, Google Chrome, Mozilla Firefox, Opera and other popular online search applications. These instructions will help you restore your browser’s default search page previously modified by hijackers, remove all unwanted search bars (toolbars) installed into your browser by adware programs, and get back to your initial browser settings that are personalized by you only, instead of the settings suggested by browser hijackers (redirecting trojans).
Introduction to browser redirection and browser hijackers
Search engine redirection problem (often referred to as a Google redirection problem) is, no doubt, a very serious and quite annoying issue for many active Internet users these days. They speak of Google redirection because most often they use Google as their search engine. Yet, such problems might occur with any search engine, including Yahoo, AOL, Bing, etc. Why do some people create applications that modify your browser settings, set up certain web sites as the default search pages and cause search redirections via these sites? The answer to these questions is quite predictable and understandable. Through installing these redirecting toolbars their owners have an opportunity to advertise various products or services together with the search results that are summarized in the redirected page. Obviously, this can bring a tremendous amount of money for developers and owners of browser hijackers. They can either promote their own commodities or services or act as promoters for other companies, their goods and services offered by them. This all brings lots of money for the owners and developers of such browser hijackers.
Methods of browser hijackers’ intrusion into computers
Installation authorized by user
There are two specific methods of how browser hijackers may integrate themselves with your browser. They can do it either legally or illegally. The first method implies user’s participation in the installation process of browser hijackers. Users are directly notified about installation of a special program of browser add-on. It is clearly stated by the program that in case of installing such application the search engine will be modified, the default start page will be amended and repaced with a new one (depending on the name of browser hijacker). As a result of such installation authorized by user, a new add-on is installed, resulting search redirections through a new window that has certain web address, instead of the default blank page of your browser.
Installation without user’s permission
In many cases browser hijackers come into computers without user’s permission. If so, the installer is generally brought into your system by malware through application of certain browser vulnerabilities available. The installation procedure is hidden from user’s attention. User doesn’t even realize some unauthorized installation is taking place. If this is the case, then surely it’s fair to categorize such installer as malicious and potentially unwanted applications that surely doesn’t use legal ways of entering your system. There are many examples of such malicious browser hijackers that don’t even ask for user’s consent when getting inside the computer.
Software through which browser hijackers and add-ons are installed
The majority of browser hijackers is bundled with other programs which users can easily download online, and then install onto their computers. These can be either freeware or shareware applications. The installers of such applications most often clearly indicate that they will install browser add-ons by default. Yet, the option is given to users to uncheck the respective box and simply install the program of their initial preference. Sometimes users fail to read the install wizard instructions carefully – this is how they install many extras, including browser add-ons that actually hijack the start page of your default browser. There are, in fact, many programs with their installers bundled with those of browser hijackers. As examples we can recall mp3 players, video players and codecs, pdf converters, etc. Yet, in many cases hijackers may be spread through direct participation of trojan horses and other forms of malware, which is obviously the result of poor anti-spyware protection level of your computer.
Lists of recommended steps to fix browser redirection problem:
- Remove all adware, browser hijackers and other unwanted programs through the Control Panel of your computer.
- Scan your system with powerful antivirus program.
- Check the Local Area Network (LAN) settings of your system.
- Check if DNS settings have been amended by browser hijacker.
- Check browser add-ons. Remove all unknown or suspicions add-ons detected (enabled).
- Checking Windows HOSTS file contents
- Scan your computer with Kaspersky’s TDSS Killer (TDSSKiller) to get rid of malware that belongs to Rootkit.Win32.TDSS family.
- Consider using CCleaner to remove all undesirable system/temp files and browser cache.
- Consider running adware-cleaning applications.
- Restoring desktop shortcuts of hijacked browsers.
- Reset your Router to the factory default settings.
Step #1. Removing adware and browser hijackers through the Control Panel of your PC.
It is of primary importance to first get rid of all adware programs and browser hijackers through Add/Remove Programs section of your Control Panel (when using Windows XP), or through Uninstall a program section of Control Panel in Windows Vista, Windows 7 and Windows 8). For this purpose please refer to the Start Menu. Choose Control Panel, and then go to Add/Remove Programs. Likewise, when using Windows Vista, Windows 7 or Windows 8, select Control Panel and choose Uninstall a Program.
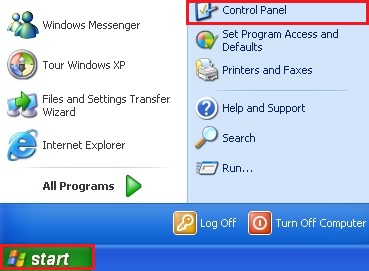
Now, with Windows 8 things are a little bit different. What you should do is just direct the mouse pointer to the right corner of the screen, and then select Search from the list, and search for “Control Panel“.

In the respective section of Search window, type “Control Panel“, and you will see the search results as follows:

So, after you’ve opened the sections Add/Remove or Uninstall a Program, carefully browse through the contents of presently installed applications and get rid of particular adware or browser hijacker, toolbar, search bar or anything else that has the name similar to that site through which your browser redirects your search. Keep in mind that if such program is in the list of installed programs, then it appeared there because of your direct participation in its installation process. You may actually click “Installed programs” and even sorts these installed applications by date. When you find anything suspicious that might cause browser redirection, select this application and click Remove. When using Windows Vista, Windows 7 or Windows 8, choose Uninstall in the upper part of the window. Once the program is successfully removed make sure you close the Control Panel window.
Step #2. Scanning computer with effective malware removal tool.
There are many working and reliable anti-virus programs these days. The degree of their effectiveness depends on various factors, primarily on how often their anti-malware databases are updated in order to effectively tackle all virus alterations and modifications. The majority of viruses in the cyber world today don’t last long in their initial shape. They get regularly amended by their developers in order not to be tracked (detected) by security applications. So, you should be very selective when considering security application for your PC. You might choose several programs, not just one. Make sure that you have the kind of security application that has the powerful module of online (real-time) protection against all contemporary threats and infections. We recommend you to choose the program that we display in the right-upper section of this blog. We in particular recommend running Plumbytes Anti-Malware that can be downloaded below.
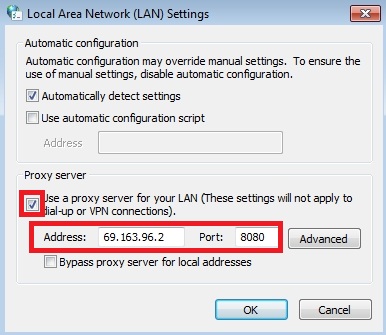
Step #3. Checking the Local Area Network (LAN) settings.
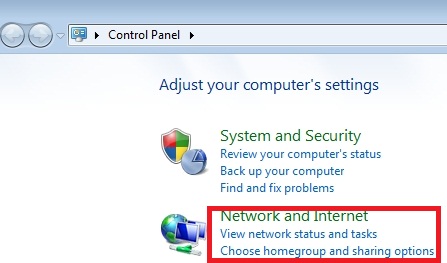
- Go to “Start” Menu and again select “Control Panel“.
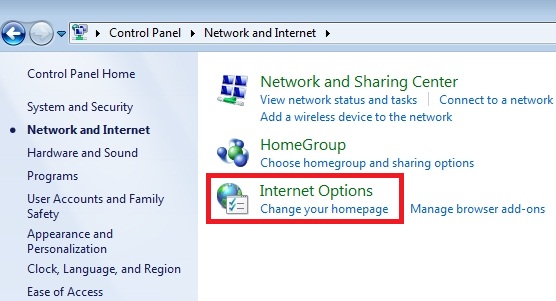
- Choose “Network and Internet“.
- Choose “Internet Options“.
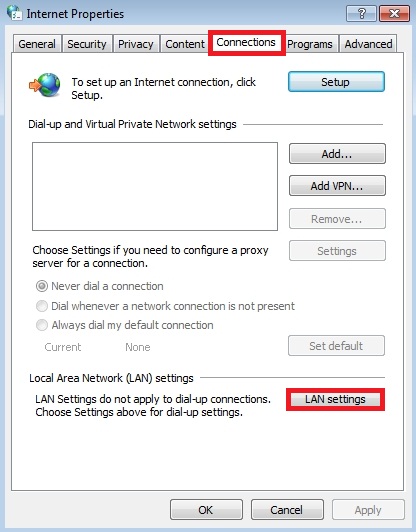
- Go to “Connections” tab, afterwards click “LAN settings” button.
- Remove (uncheck) the checkbox under “Proxy server” option and click OK.

Step #4. Checking DNS settings.
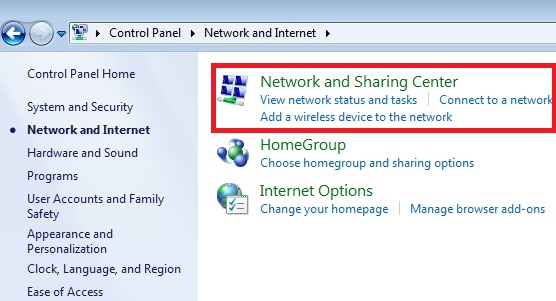
- Go to “Start” Menu and refer to “Control Panel“.
- Choose “Network and Internet“.
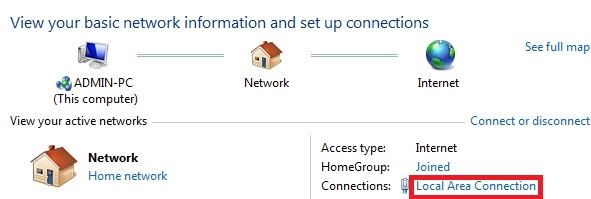
- Go to “Network and Sharing Center”.
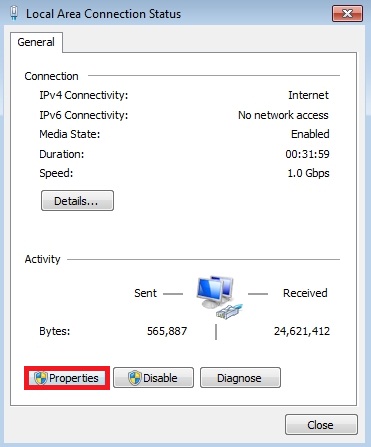
- Select “Local Area Connection”.
- Choose “Properties”.
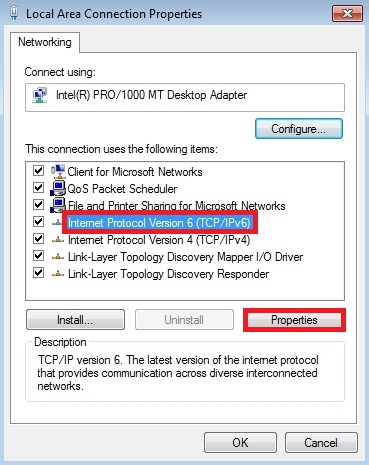
- Choose “Internet Protocol Version 6 (TCP/IP V6)” and select “Properties”.
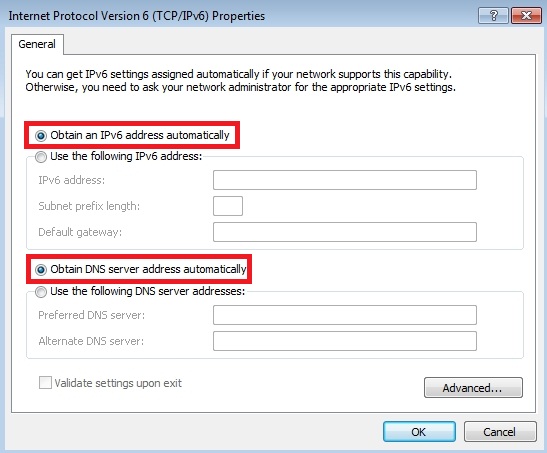
- Select “Obtain DNS server address automatically” and click OK.


Step #5. Checking browser add-ons. Removal of all unknown or suspicions add-ons identified.
- Go to “Start” Menu and direct your mouse pointer towards “Control Panel“.
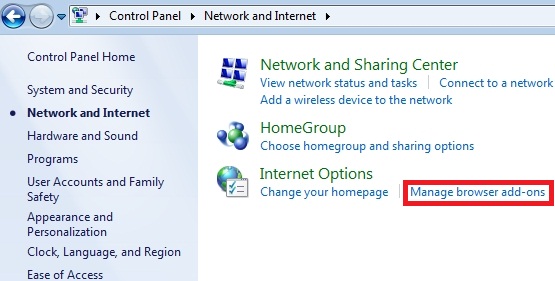
- Choose “Network and Internet“.
- In the section “Internet Options” choose “Manage browser add-ons“.
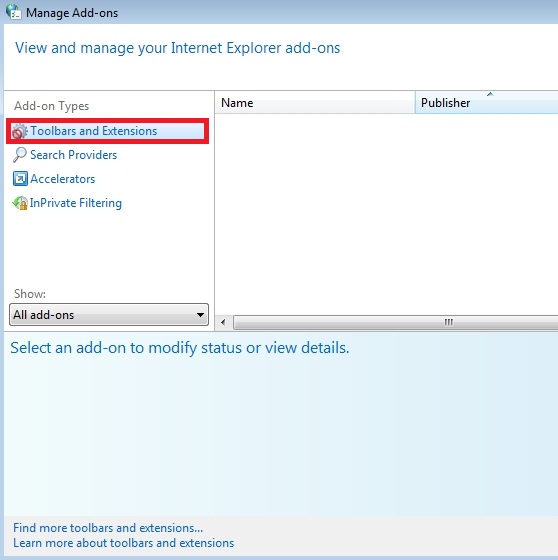
- Get rid of any unknown or suspicious Toolbars or Search Providers.


Important! For more information on managing browser add-ons please go to this guide for additional information on managing add-ons and extensions depending on the type of your default browser – https://www.system-tips.net/managing-browser-add-ons-to-fix-search-engine-redirection-problem/ .
Step #6. Checking Windows HOSTS file contents
- Go to: C:\WINDOWS\\system32\\drivers\\etc.
- Double-click “hosts” file to open it. Select the option to open it using Notepad.
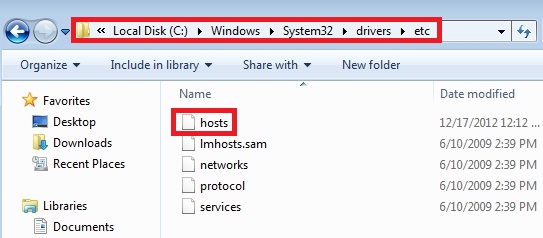
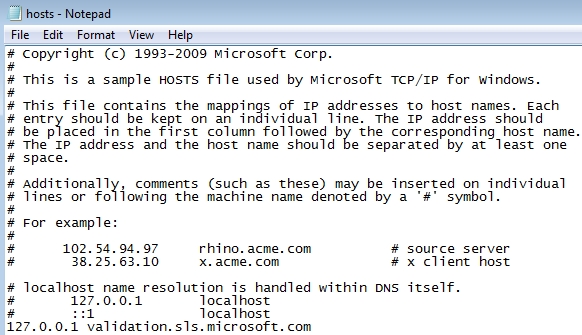
li>The “hosts” file must look the same as in the image below. There should be just one line: 127.0.0.1 localhost in Windows XP and 127.0.0.1 localhost ::1 in Windows Vista/Seven. If there are more, then remove them and apply changes.
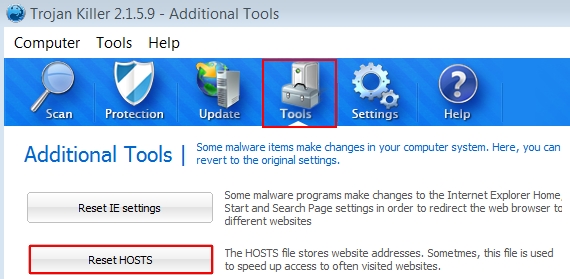
Important! You may also choose the feature to reset your HOSTS file using the Tool of Plumbytes Anti-Malware as shown at the image below:
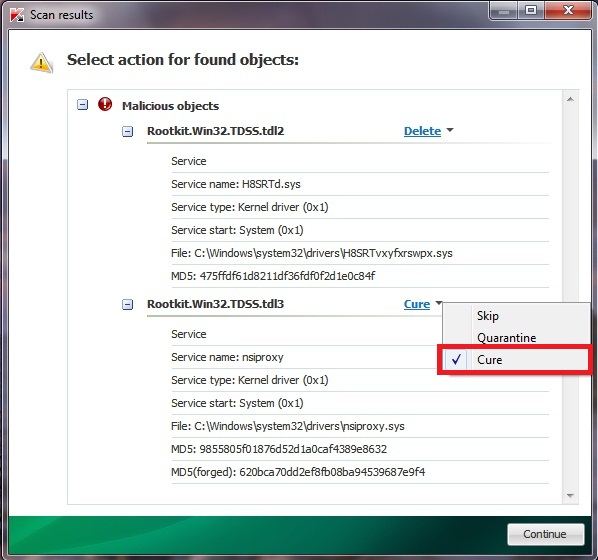
Step #7. Scanning with Kaspersky’s TDSS Killer (free application).
- Download and run TDSS Killer from this link.
- Wait for the scan and disinfection process to be completed. Shut down all applications and hit “Y” key to reboot your system.
Step #8. Using CCleaner.
CCleaner is the application that can be easily googled and thus downloaded. When running it, keep in mind that it will clean the entire “Temp” directory of your computer, so if you have anything important in it please first save the data you need into other locations.
Step #9. Running adware-cleaning applications.
This option is also recommended. There are many working and effective automatic solutions that might be helpful to you when dealing with browser redirection issues. Again, Google will point you in the right direction to find the adware-cleaning program of your preference.
Step #10. Cleaning shortcuts of browsers that have been hijacked.
This step applies only to certain browser hijackers which are extremely severe. However, it is strongly recommended that you perform this important step. So, search for your browser shortcut depending on where it is located – on Desktop, in Taskbar or in Start Menu. Now, right-click it and select Properties:
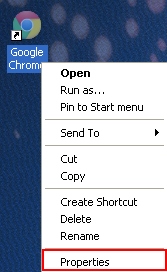
Click Shortcut tab and get rid of any name of the site through which search redirection occurs from the Target field and click OK to apply changes. Generally, there should be only the path to the executable file of your browser, nothing else. See how this is represented on the example of Google Chrome browser:
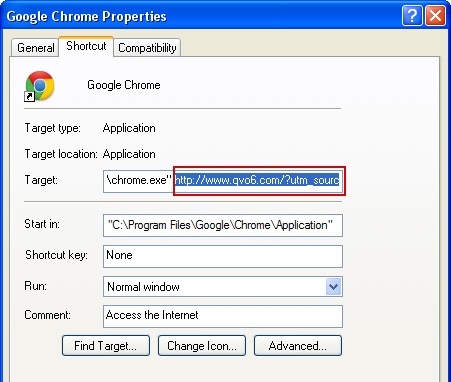
Step #11. Resetting Router to factory default settings.
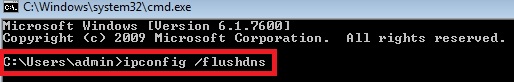
At this point we should emphasize that resetting the router to the factory default settings is the option to which you should adhere only if other tricks above didn’t work. So, this recommendation should only be followed if in spite of all the above-mentioned recommendations you still have the redirect virus on your machine. Then you should flush DNS cache:
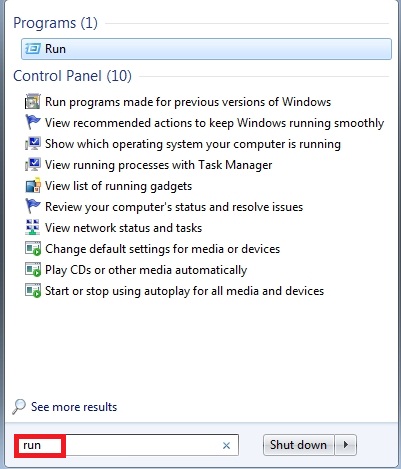
- Click “Start” and in the open space write down “run” This surely applies to Windows Vista and Windows 7 operating systems. With Windows XP you may fine “Run…” once you click “Start” menu option. With Windows 8 you may direct your mouse pointer towards the right section of your desktop until the menu comes up with “Search” tab. This is where you may look for Run command.
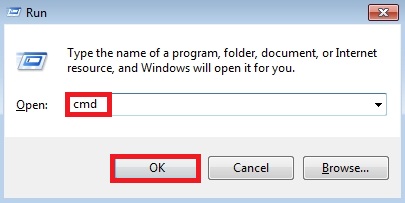
- Type “cmd” without quotation marks.
- In a new window please type “ipconfig /flushdns” without quotation marks and press Enter.
We hope this information has helped you removing browser hijackers from your computer that surely cause a tremendous load of problems for our brains. In spite of the fact they’re annoying, they also make our systems more and more vulnerable to further attacks of malwares. So, you’ve surely made a good decision to remove them off your computer. Keep in mind that there are various modifications and names of browser hijackers. Some of them are quite simple to remove, whereas others require more time to be deleted. If you have any difficulties getting rid of them, simply let us know. We’ll do all our best to assist you the best we can. Again, true comments are always welcome, so why don’t you drop a line to share what you think about this guide and whether you benefited from it? If this tutorial has helped you, share this information with other people so that they would know how to deal with such serious problems as the issues of browser redirection. Good luck!

My info on number ten says proxy server. Should I delete that? thanks. I think this site helps
my info on number 6 says proxy. Should I remove that?
Windows defender keeps bringing this up Win32/Dartsmound. Scanns using Updated windows defender and mal ware bytes are not able to find anything. Any reccomendations?
thx alot keep work doing like this