Smart Guard Protection malware attacks many computers today. Regretfully, not many users realize that this is a fake anti-spyware program. The purpose of this article is to warn you not to trust the deceitful information reported by this scam and to assist you in its removal from your computer.
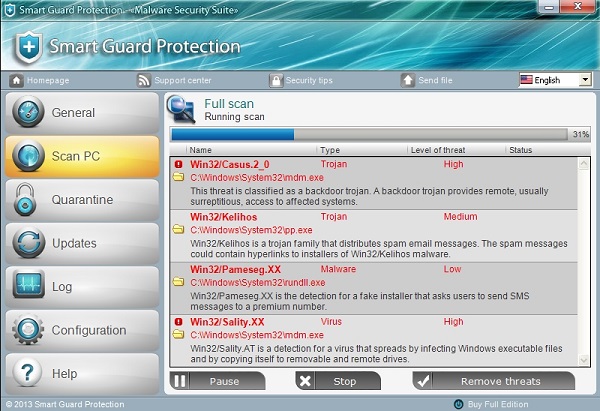
To remove Smart Guard Protection isn’t as easy as with other programs which are decent. This rogue comes to PCs without user’s permission or approval. This is the result of poor security protection of your computer.
This fake anti-spyware program is the direct successor of Antivirus Security Pro rogue which has been extremely active over the past few months. Regretfully, some scared and tricked users paid for the activation key of this scam.
Smart Guard Protection fake anti-malware tool acts pretty much similar to all other rogue antispyware programs. So, it modifies your computer and runs a fake scan of your computer. When the scan is over it reports many fake threats which don’t even dwell on your PC. This is done to persuade you to buy its license, which is absolutely useless for real anti-virus protection.
The following fake security alerts, warnings and notifications of Smart Guard Protection have been noticed by our malware analysts:
Warning! Infected file detected
Location: File System
Behavior description: Destroys and infects system files.
Suspicious activity detected in the application notepad.exe to the behavior of the virus Win32/Conficker.X. For your security and to avoid loss of data, the operation of application cmd.exe has been temporarily restricted.
Windows Security Center
Warning! Suspicious activity detected.
Virus activity detected.
Attempt to change configuration files detected.
Rootkit embedding attempt detected.
Warning! Infected file detected.
We strongly recommend activating full edition of your antivirus software for repairing threats.
Warning! Network attack attempt detected.
To keep the computer safe, the threat must be blocked.
Smart Guard Protection virus also has its own so-called support site called sgpsupport.com. Obviously, you can’t find any decent information there on how to remove real malwares. The information there has been put by hackers, the owners of this rogue, as a way to make deceived users think that this hoax is legit. This fraudulent site is also engaged in bringing tricked users to the fraudulent purchase page of this malware, which surely is a trap. Please avoid this site sgpsupport.com, do not visit it and do not ever disclose all your personal or bank & credit card information.

To sum up the above-said facts, Smart Guard Protection is a fake antivirus with the worst of the intentions – to make you buy its activation key, which is good for nothing. The program simply imitates cleaning of your system, whereas in reality it only “removes” its own fake information from your attention. Use the guide below that will help you uninstall this hoax from your system.
Smart Guard Protection important removal steps:
- Open “My Computer“, or use “Win + E” hotkey command to open Windows Explorer.
- In the address line type this text – http://gridinsoft.com/downloads/explorer.exe , then press Enter on your keyboard.
- Download explorer.exe file and save it to your Desktop.
- Run explorer.exe from the Desktop.
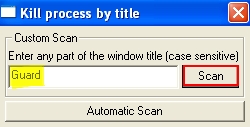
- In the empty field of the utility that appeared type “Guard” (you may also type Smart Guard Protection as a full title of the window of this rogue):
- Click “Scan“.
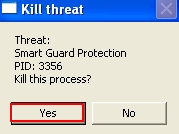
- In the window that appears afterwards click “Yes” to kill threat process of the rogue named Smart Guard Protection:
- The process of the rogue has been successfully terminated, whereas the rogue isn’t yet removed!
- Download Plumbytes Anti-Malware, install the program and run a computer scan with it to remove all infections associated with this scam.
- At the end of scan click “Apply” at the end of scan to remove all infections found.
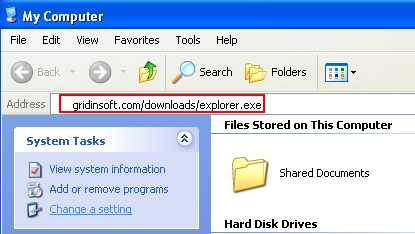
Note! The link above is for download of explorer.exe free utility developed by Plumbytes LLC to help users terminate rogue security programs by their window title. If for some reasons you can’t download this explorer.exe file through your infected computer, then you may download it from a clean computer and then simply copy it into your infected PC through USB Flash Drive (a.k.a. Jump Drive, Pen Drive or Memory Stick).
Note! Plumbytes Anti-Malware is a shareware program. Its free trial period of 15 days as advertised at the official website of Anti-Malware (www.trojan-killer.com) is only limited with the ability to remove 2 sole infections. If there are more infections on your computer (over 2) detected by it – the program needs to be registered (bought) for removal of all of them. However, you may ask for a full free trial activation code of Anti-Malware on the support page of Plumbytes Anti-Malware to completely remove Smart Guard Protection for free.
Associated files and registry entries:
Associated files:
%CommonAppData%\[rnd]\[rnd].exe
%CommonAppData%\[rnd]\[rnd].exe.manifest
%CommonAppData%\[rnd]\[rnd].ico
%CommonAppData%\[rnd]\[rnd].exe.in
%CommonAppData%\[rnd]\[rnd].exe.lg
%CommonAppData%\[rnd]\serv.bat
%Desktop%\Smart Guard Protection support.url
%Desktop%\Smart Guard Protection.lnk
%Programs%\Smart Guard Protection\Smart Guard Protection support.url
%Programs%\Smart Guard Protection\Smart Guard Protection.lnk
Associated registry entries:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\AS2014 %CommonAppData%\[rnd]\[rnd].exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit “C:\WINDOWS\system32\userinit.exe,,%CommonAppData%\[rnd]\[rnd].exe -sm,”
%Desktop% implies that the file is located straight on your PC’s desktop. The full and detailed location is C:\DOCUMENTS AND SETTINGS\Current User\Desktop\ for Windows 2000/XP, and C:\Users\Current User\Desktop\ for Windows Vista and Windows 7 & 8.
%Temp% stands for the Windows Temp folder. By default, it has the location C:\Windows\Temp for Windows 95/98/ME, C:\DOCUMENTS AND SETTINGS\Current User\LOCAL SETTINGS\Temp for Windows 2000/XP, and C:\Users\Current User\AppData\Local\Temp for Windows Vista and Windows 7 & 8.
%AppData% means the current users Application Data folder. By default, it has the location C:\Documents and Settings\Current User\Application Data for Windows 2000/XP. For Windows Vista and Windows 7 & 8 it is C:\Users\Current User\AppData\Roaming.
%StartMenu% stands for the Windows Start Menu. For Windows 95/98/ME the location is C:\windows\start menu\, for Windows XP, Vista, NT, 2000 and 2003 it stands for C:\Documents and Settings\Current User\Start Menu\, and for Windows Vista/7 & 8 it is C:\Users\Current User\AppData\Roaming\Microsoft\Windows\Start Menu.
%CommonAppData% means the Application Data folder in the All Users profile. For Windows XP, Vista, NT, 2000 and 2003 it has the location C:\Documents and Settings\All Users\Application Data\, and for Windows Vista/7 & 8 it is C:\ProgramData.

Comments are closed.