This is the guide explaining removal of Vista Security Cleaner Pro. This particular program is a representative of MultiRogue 2013 fake antiviruses, also referred to as name-changing rogues of 2013 malware generation. Certain decent security applications detect this malware as FakeRean. Other detect it differently. No matter how exactly this rogue is detected, the general understanding in security companies and malware removal blogs regarding this hoax is exactly the same. The application that is named Vista Security Cleaner Pro is definitely not a program that can render security for your Vista operating system.
So, Vista Security Cleaner Pro attacks Vista OS. Even though, the same malicious installer may cause other malwares (with other names) to appear on computers with other operating systems. We’ve already published the articles on XP Security Cleaner Pro and Win 7 Security Cleaner Pro. As you see, these three programs are very similar in their design and the pattern of behavior on the attacked workstations. Here is how Vista Security Cleaner Pro looks like once it attacks Windows Vista computers:
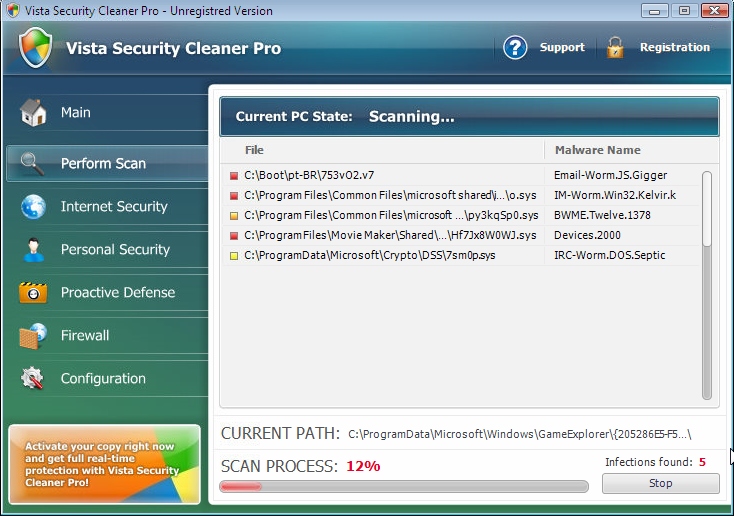
Like many other rogues, this program comes to computers without user’s permission. Users, in fact, don’t even participate in the installation process of this fake anti-spyware tool. Additionally, the malware amends your system settings in order to be self-launched automatically together with every system startup. As a result of such unauthorized actions, the hoax comes up in front of your eyes each time you have some important assignment to perform on your computer. Surely, this fact is very annoying, cause this draws your attention out of important issues towards dealing with Vista Security Cleaner Pro and its many fake system alerts, warnings and notifications.
Fake system scans of Vista Security Cleaner Pro are quite expected to take place right after the hoax is self-launched. The reason why the program runs all such bogus scans is because it attempts to make users extremely scared about the condition of their computers. Yet, the truth is that all such infections identified by this rogue AV are totally fabricated. These threats reported by Vista Security Cleaner Pro are either legitimate Windows files, or some items which don’t even dwell on your hard drive.
The program called Vista Security Cleaner Pro has in mind to make you buy its fake licensed version, which is not able to remove real infections. Sooner or later the rogue will tell that in order to have those bogus threats removed you definitely need to buy its license. Doing so, of course, is a serious mistake, and we do hope that you will never commit such a mistake in your life. If you’ve bought this scam by mistake, then please dispute the charges made via your bank card immediately. Finally, to get rid of Vista Security Cleaner Pro malware from your computer please follow the guidelines below.
Vista Security Cleaner Pro removal steps:
- First, ignore all scary alerts of Vista Security Cleaner Pro scam.
- Use “Win + E” hotkey command to open Run command window.
- In the address line type the direct download link of Plumbytes Anti-Malware http://trojan-killer.net/download.php and click “Enter“.
- Save the installer of Plumbytes Anti-Malware onto your desktop.
- Right-click the installer with your mouse and run it as Administrator.
- Install Anti-Malware. Uncheck the box “Run Anti-Malware” at the end of installation process.
- Right-click the desktop icon of Plumbytes Anti-Malware and run Anti-Malware as Administrator.
- Update Anti-Malware and run scan with it.
- Once the scanning has been completed, click “Remove Selections” to remove all items associated with Vista Security Cleaner Pro.
- Restart your computer and repeat scan if necessary.
- Share this malware removal guide with your colleagues, relatives and friends.
Removal video at YouTube:
Download recommended malware removal solution:
Associated virus files:
%CommonAppData%\[random characters and numbers]
%LocalAppData%\[random characters and numbers]
%LocalAppData%\[random 3 characters].exe
%Temp%\[random characters and numbers]
%AppData%\Roaming\Microsoft\Windows\Templates\[random characters and numbers]
Associated registry entries:
HKEY_CURRENT_USER\Software\Classes\.exe “(Default)” = ‘[random]’
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command “(Default)” = “%LocalAppData%\[random 3 characters].exe” -a “%1” %*
HKEY_CLASSES_ROOT\[random]
HKEY_CURRENT_USER\Software\Classes\[random] “(Default)” = ‘Application’
HKEY_CURRENT_USER\Software\Classes\[random]\DefaultIcon “(Default)” = ‘%1’
HKEY_CURRENT_USER\Software\Classes\[random]\shell\open\command “(Default)” = “%LocalAppData%\[random] 3 characters].exe” -a “%1” %*
HKEY_CLASSES_ROOT\.exe\shell\open\command “(Default)” = “%LocalAppData%\[random 3 characters].exe” -a “%1” %*
HKEY_CLASSES_ROOT\ah\shell\open\command “(Default)” = “%LocalAppData%\[random 3 characters].exe” -a “%1” %*
HKEY_CLASSES_ROOT\ah\shell\open\command “IsolatedCommand”
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command “(Default)” = “”%LocalAppData%\[random 3 characters].exe -a “C:\Program Files\Mozilla Firefox\firefox.exe””
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command “(Default)” = “”%LocalAppData%\[random 3 characters].exe” -a “C:\Program Files\Mozilla Firefox\firefox.exe” -safe-mode”
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command “(Default)” = “”%LocalAppData%\[random 3 characters].exe” -a “C:\Program Files\Internet Explorer\iexplore.exe””
File Location Implications:
%Desktop% implies that the file is located straight on your PC’s desktop. The full and detailed location is C:\DOCUMENTS AND SETTINGS\Current User\Desktop\ for Windows 2000/XP, and C:\Users\Current User\Desktop\ for Windows Vista and Windows 7.
%Temp% stands for the Windows Temp folder. By default, it has the location C:\Windows\Temp for Windows 95/98/ME, C:\DOCUMENTS AND SETTINGS\Current User\LOCAL SETTINGS\Temp for Windows 2000/XP, and C:\Users\Current User\AppData\Local\Temp for Windows Vista and Windows 7.
%AppData% means the current users Application Data folder. By default, it has the location C:\Documents and Settings\Current User\Application Data for Windows 2000/XP. For Windows Vista and Windows 7 it is C:\Users\Current User\AppData\Roaming.
%StartMenu% stands for the Windows Start Menu. For Windows 95/98/ME the location is C:\windows\start menu\, for Windows XP, Vista, NT, 2000 and 2003 it stands for C:\Documents and Settings\Current User\Start Menu\, and for Windows Vista/7 it is C:\Users\Current User\AppData\Roaming\Microsoft\Windows\Start Menu.
%CommonAppData% means the Application Data folder in the All Users profile. For Windows XP, Vista, NT, 2000 and 2003 it has the location C:\Documents and Settings\All Users\Application Data\, and for Windows Vista/7 it is C:\ProgramData.