Windows Prime Accelerator is a rogue antivirus that pretends to be a good program to convince users into buying its so-called “ultimate protection” of this scam. Windows Prime Accelerator comes into PCs by means of fake Microsoft Security Essentials alerts that will force its entry on the compromised PC by exploiting software vulnerabilities and due to the weak protection by legitimate security programs. Then it will connect to a remote host to download and install this hoax without users approval.
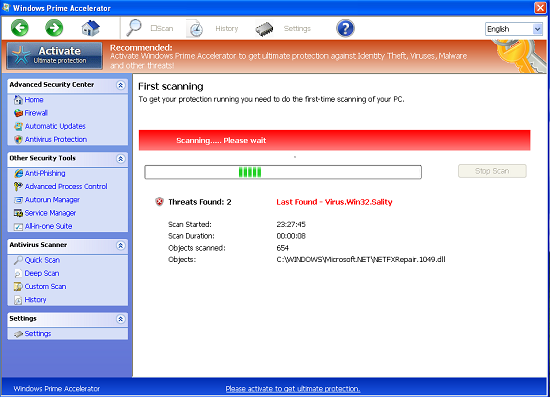
Windows Prime Accelerator virus on the system will cause a lot of operation abnormalities. Internet browser redirects to unwanted web pages and causes even more threats. Applications will be blocked from running and installed antivirus application will be disabled. In addition, the most common symptoms are a frequent and excessive pop-up alerts coming from Windows Prime Accelerator stating that PC is infected with different types of threats.
When this virus gets inside of your system you will see a warning that your PC is under some kind of virus attack. Keep in mind that Windows Prime Accelerator initially was elaborated for the only fraudulent aim – that is to steal money from unaware users, thus, additionally to scam notices, it will suggest you to register its so-called “ultimate protection”. Be confident that this is the program that causes destruction and mess with users’ systems. At the same time, so many users are being tricked with it and never get any decent aid in response. Hence, if you encounter its occurrence on your PC, immediately take all the necessary steps in order to get rid of Windows Prime Accelerator virus. Failure to do so can cause essential damage to the attacked PC and your important, personal information may be transferred to some cyber criminals.
These operations have the main goal – to trick users in obtaining the “ultimate protection” of Windows Prime Accelerator. Never be tricked like that, instead delete Windows Prime Accelerator virus as soon as its occurence is visible to prevent further damage it may bring to an infected computer. Use only some decent security program to completely get rid of this hoax and all of its hidden components. We recommend you to use Plumbytes Anti-Malware for this purpose.
Software necessary for Windows Prime Accelerator virus removal:
Windows Prime Accelerator removal steps:
- In Windows Prime Accelerator click “?” Menu button anc click “Register”:
- Paste this product key – 0W000-000B0-00T00-E0022 exactly as shown at the image below, then click “Register“:
- Afer registration download Plumbytes Anti-Malware without any restrictions on the part of the rogue, scan your PC with Plumbytes Anti-Malware and remove all infections detected by clicking “Apply” button at the end of scan.
- Restart your computer and repeat scan.


Windows Prime Accelerator similar removal video at YouTube:
Beware of ways how Windows Prime Accelerator is spread today:
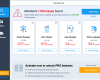
Windows Prime Accelerator users various vulnerabilities of browsers like Internet Explorer, Google Chrome, Mozilla Firefox, Opera and many others for the interference into your computer. For example, you might get the following scary alert, supposedly coming from Microsoft Antivirus:
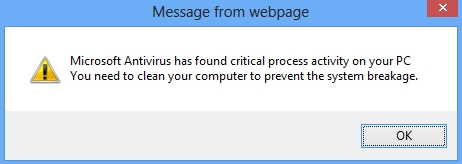
Microsoft Antivirus has found critical process activity on your PC. You will need to clean your computer to prevent the system breakage.
If you actually click the “OK” button as shown at the image you will have another fake alert, not associated at all to Microsoft Security Essential Alert, but yet claiming to be such:
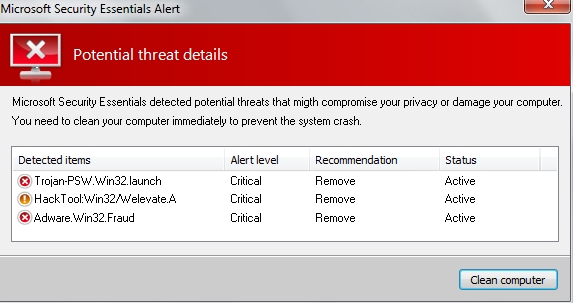
Microsoft Security Essentials Alert
Potential threat details
Microsoft Security Essentials detected potential threats that might compromise your privacy or damage your computer. You need to clean your computer immediately to prevent the system crash.
Detected items:
– Trojan-PSW.Win32.launch
– HackTool:Win32/Welevate.A
– Adware.Win32.Fraud
Associated files and registry entries:
Related files:
%AppData%\svc-[rnd].exe
%CommonAppData%\connector.swf
%Programs%\Windows Prime Accelerator.lnk
%Desktop%\Windows Prime Accelerator.lnk
Related registry entries:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\PrSft %AppData%\svc-[rnd].exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\k9filter.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\k9filter.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe\Debugger svchost.exe
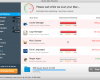
Fake security alerts, notifications and warnings of Windows Prime Accelerator scam:
Firewall has blocked a program from accessing the Internet
C:\Program Files\Internet Explorer\iexplore.exe
is suspected to have infected your PC.
This type of virus intercepts entered data and transmits them
to a remote server.
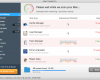
Error
Trojan activity detected. System integrity at risk.
Full system scan is highly recommended.
Error
System data security is at risk!
To prevent potential PC errors, run a full system scan.