Windows Accelerator Pro is a fake antivirus program with the only intention – to make scared users buy its so-called “ultimate protection”, or a product key. The rogue promises to render best security services for your computer on the condition that you pay for its registered version. In reality, this application is absolutely useless when it comes to rendering real anti-malware protection for your computer.
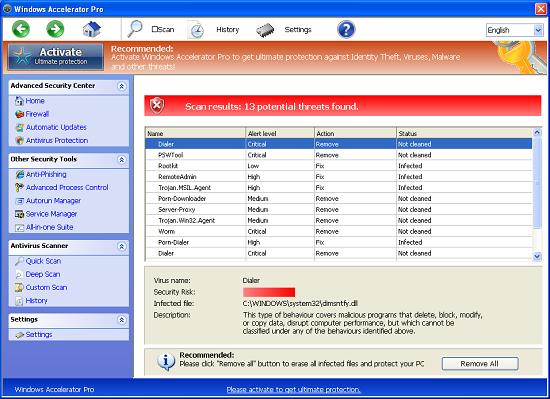
Users find it very difficult to remove Windows Accelerator Pro rogue antispyware. The malware has been designed in a very professional manner to make it really hard for users to get rid of it. This is why all regular attempts to uninstall Windows Accelerator Pro turn out to be absolutely vain.
Windows Accelerator Pro fake antivirus uses illegal ways for entering PCs. As a matter of fact, this often occurs through fake Microsoft Security Essential Alerts which use all possible vulnerabilities of your browser and thus come up as a special pop-up after clicking certain unsafe and infected links. Typically these fake MSE alerts report some “serious” issues with your PC, telling you to donwload some sort of a utility for system cleanup. In reality, the malware called Windows Accelerator Pro is downloaded into system.
Once inside the rogue antivirus called Windows Accelerator Pro disables your Desktop completely through hijacking it. When you start your computer you will see this rogue in the very beginning. It immediately runs a fake scan of your computer which lasts for quite a long time. It then reports all kinds of system malfunctions and various threats and infections on your system. It says that in order to get rid of them you must purchase its license, so-called “ultimate protection“.
During the fake system scan of your system by Windows Accelerator Pro and upon its completion the following fake and scary security alerts and warnings are presented:
Firewall has blocked a program from accessing the Internet
C:\Program Files\Internet Explorer\iexplore.exe
is suspected to have infected your PC.
This type of virus intercepts entered data and transmits them
to a remote server.
Error
Trojan activity detected. System integrity at risk.
Full system scan is highly recommended.
Error
System data security is at risk!
To prevent potential PC errors, run a full system scan.
You must not trust any of the deceptive statements reports by Windows Accelerator Pro virus. And, of course, buying this hoax is a serious mistake. Hopefully, you will not make it. If you have been scared into purchasing this scam you need to get in touch with your bank institution right away and dispute the charges made through your account.
AS we’ve said above, getting rid of Windows Accelerator Pro scam isn’t an easy undertaking even for tech savvy computer users. The rogue blocks Task Manager, cmd.exe and taskkill.exe commands, all your available browsers and installed security programs which are legitimate. Furthermore, you can’t find the uninstaller for this hoax simply because it is a virus which came into your system illegally. To remove Windows Accelerator Pro rogue completely and effectively we first recommend you to activate it using the following product key – 0W000-000B0-00T00-E0022 as mentioned in the instructions below. Afterwards you may completely get rid of this hoax with the help of Plumbytes Trojan Kiler as instructed in the remainder of this article.
Software necessary for Windows Accelerator Pro virus removal:
Removal steps:
- In Windows Accelerator Pro click “?” Menu button anc click “Register”:
- Paste this product key – 0W000-000B0-00T00-E0022 exactly as shown at the image below, then click “Register“:
- Afer registration download Plumbytes Anti-Malware without any restrictions on the part of the rogue, scan your PC with Plumbytes Anti-Malware and remove all infections detected by clicking “Apply” button at the end of scan.
- Restart your computer and repeat scan.


Associated files and registry entries:
Related files:
%AppData%\guard-
%AppData%\result1.db
Related registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations “LowRiskFileTypes” = “.zip;.rar;.nfo;.txt;.exe;.bat;.com;.cmd;.reg;.msi;.htm;.html;.gif;.bmp;.jpg;.avi;.mpg;.mpeg;.mov;.mp3;.m3u;.wav;”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments “SaveZoneInformation” = 1
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon “Shell” = “%AppData%\guard-
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorAdmin” = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorUser” = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “EnableLUA” = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “EnableVirtualization” = 0